Native Mobile SDKs
Offline Android and iOS components for identity capture. Works without internet connection. Quick integration into your native Apps. Tested in over 1000+ mobile devices.
View SDK Documentation 
Cloud APIs
Restful APIs that can be integrated instantly without worrying about infrastructure or auto scaling. Our battle tested AWS environment is ISO 27001:2013 certified and monitored 24x7.
View API Documentation 
On-Premise
Use our technology deployed as Docker containers in your own servers. In this set up there are no external calls outside your servers giving you total control over your data.
Contact Sales 
Cloud Dashboard (no-code)
Get started instantly and begin your identity verification projects. The dashboard provides you with everything you need to onboard your customers as per prevailing regulations.
Book a demo 

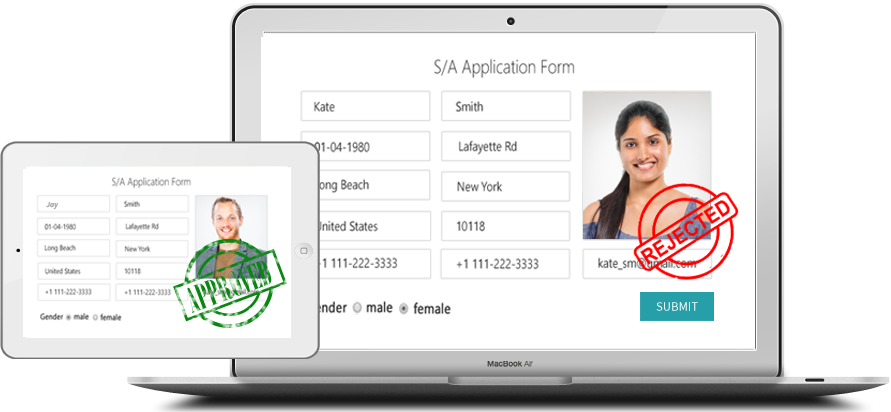

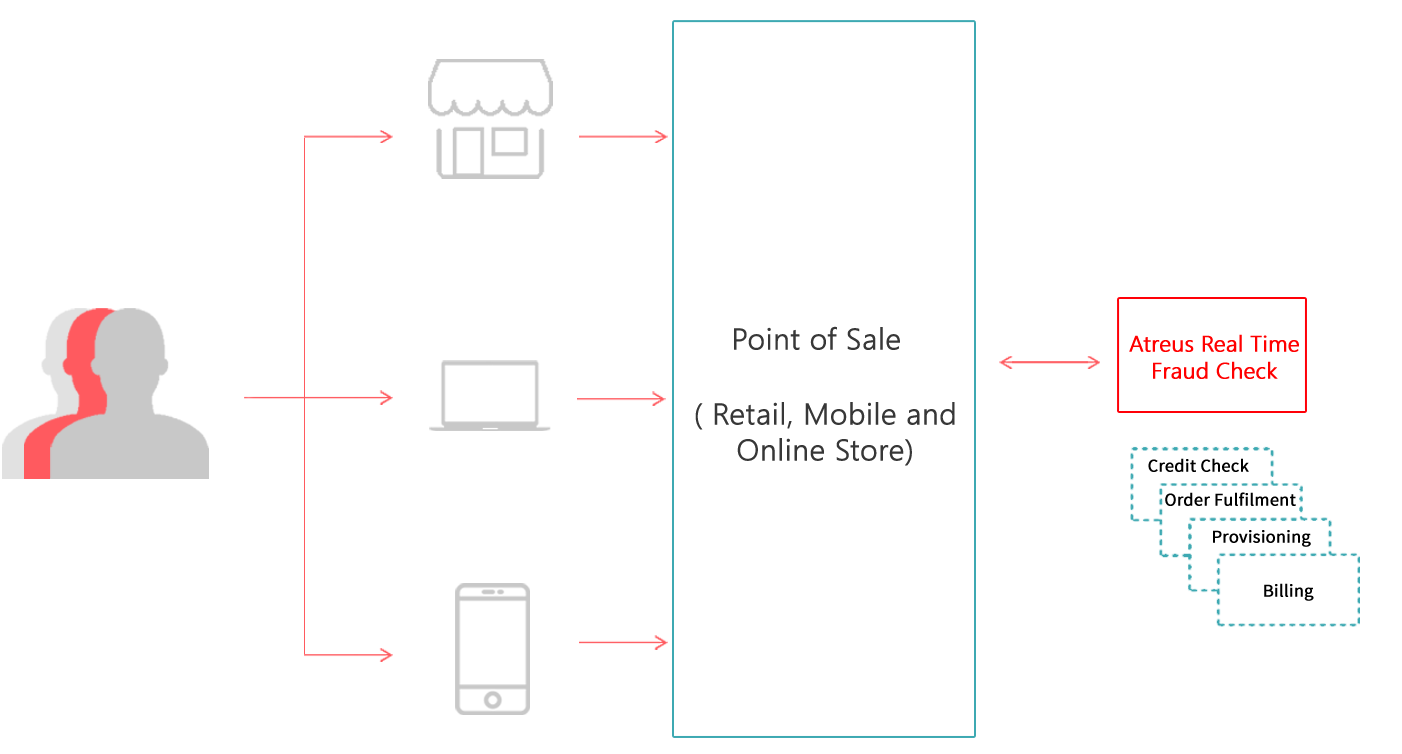
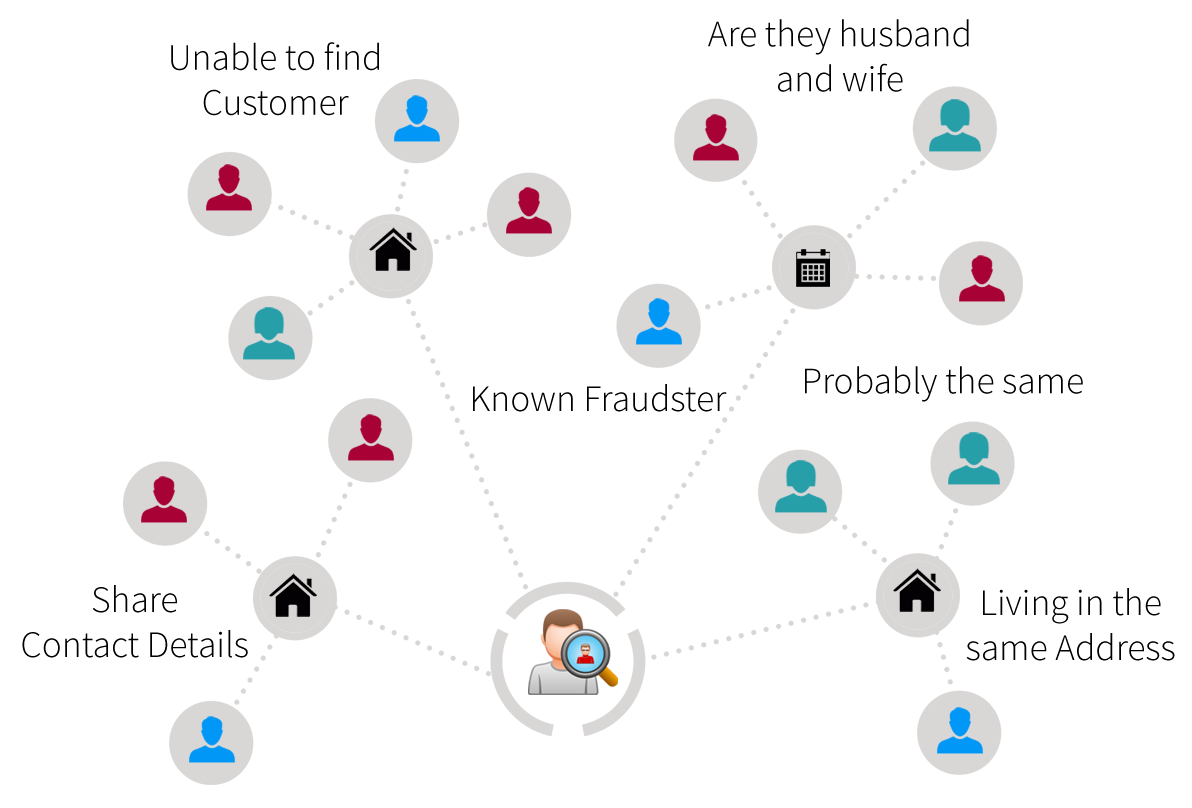
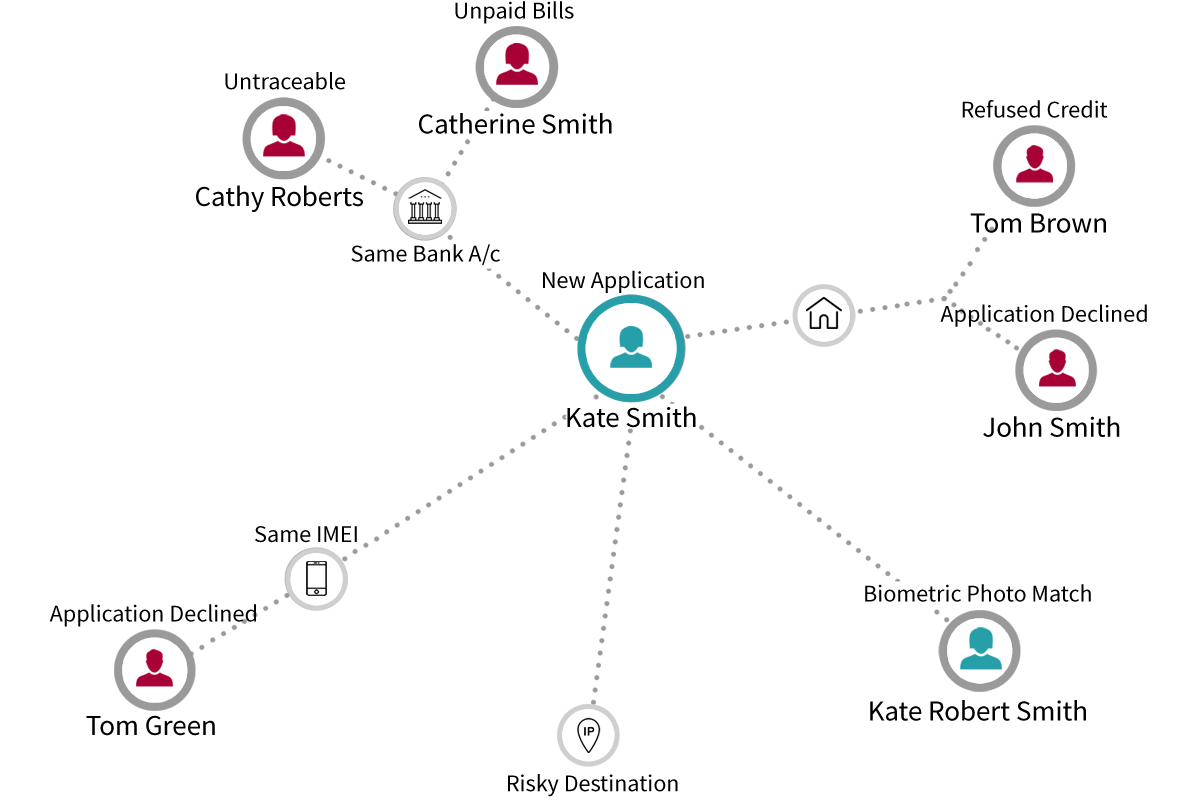

 Tell us your needs
Tell us your needs See how Atlas works
See how Atlas works  Ask us anything
Ask us anything  Build your solution
Build your solution